Azure Kubernetes Service (AKS) is a fully managed Kubernetes (K8s) offering from Microsoft on the Azure platform. AKS reduces the management overhead of running your own K8s instance while still being able to take full advantage of Container Orchestration. Microsoft takes care of the K8s health monitoring and maintenance. With AKS you only manage the agent nodes while Microsoft manages the master nodes. Also with AKS you get integration to many of the Azure services such as load balancers, RBAC, Azure storage etc.
In this blog post I am going to walk through the setup of an AKS cluster step by step. This is to serve as a intro to AKS to show how easy it is to get started with Kubernetes in Azure. In a follow up blog post I will dive into AKS more showing how to deploy an instance MySQL and WordPress containers on AKS. Before we get into the setup of AKS there are a few things to note:
- With the AKS managed service you only pay for the agent nodes within your AKS cluster. There is no cost for the master nodes and the managed service itself is free.
- At the time of this blog post AKS only supports Linux containers. There is a work around for this until Windows nodes and containers come to AKS.
- AKS is only available in the following Azure regions:
-Australia East
-Canada Central
-Canada East
-Central US
-East US
-East US2
-Japan East
-North Europe
-Southeast Asia
-UK South
-West Europe
-West US
-West US 2 - The Kubernetes API server is exposed as a public fully qualified domain name (FQDN). Access should be restricted on this. It can be restricted using K8s RBAC and AAD.
Deploy AKS
Housekeeping is done, now let’s get into the deployment of AKS. The first thing you need to do within the Azure portal is go to Create a resource and search on Kubernetes. Select the Kubernetes Service.

Click on create.
You will now see the setup. The setup consists of the following sections shown in the following screenshot:

Let’s walk through each section.
Basics
Here you need to give your AKS instance a name, select the region, K8s version, DNS prefix, and number of nodes and count.


Authentication
Kubernetes has its own RBAC within its authentication and authorization system. Azure Active Directory (AAD) can be integrated with this for authentication. Once the AAD and K8s integration is setup AAD users can be used for Kubernetes role-based access control (RBAC) to cluster resources. Select yes to enable RBAC and integration with AAD.

It is recommended to setup your own service principle in AAD. For this blog post I let the deployment create one. The service principle is used by K8s for managing Azure cloud resources attached to the cluster. The service principle interacts with Azure APIs. For example when you setup a load balancer service in K8s AKS creates and Azure load balancer. The service principle is what is used for authentication to create the load balancer.
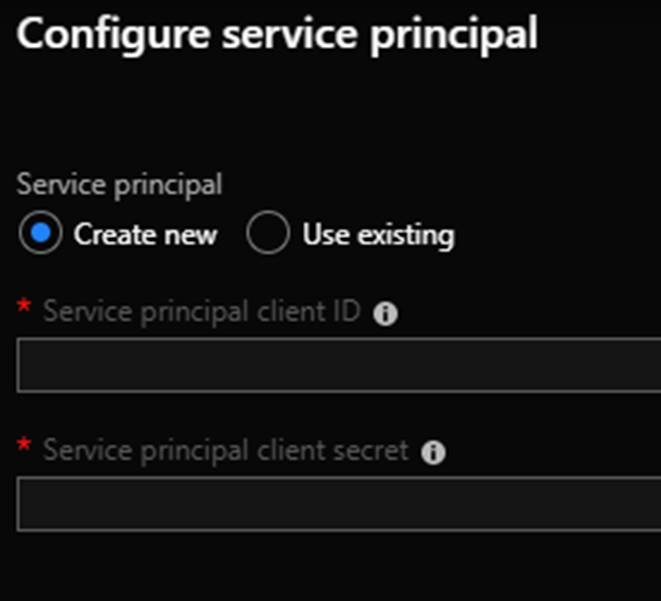
Networking
In this section you chose what you want for networking with AKS. If you select basic AKS will create all needed VNets, Subnets, NSG’s etc. AKS clusters cannot use the following ranges 169.254.0.0/16, 172.30.0.0/16, and 172.31.0.0/16. If you select advanced you can chose an existing VNet or create a new one specifying the subnet, IP range and DNS settings etc. You would select Advanced if you need more control over the virtual networking.

HTTP application routing is used to make application endpoints publicly accessible in the AKS cluster. Enabling this essentially configures an Ingress controller in the AKS cluster. When getting started with AKS I recommend leaving this disabled and doing more research on K8s Ingress Controllers here https://kubernetes.io/docs/concepts/services-networking/ingress as there are other options making applications publicly accessible. In the meantime while getting started with AKS you can use the load balancer service type for external access to your applications running on AKS.
Monitoring
With AKS you have the option to utilize Container monitoring from Azure Monitor. This will give you performance and health monitoring. The monitoring data comes directly from an AKS cluster or from all the AKS clusters via Azure Monitor more specifically Log Analytics. In the future I plan to post a deeper blog about monitoring AKS.
If you chose to enable this you will need to setup a new Log Analytics workspace or use an existing one.

Tags
You can set tags for the AKS cluster.

Create
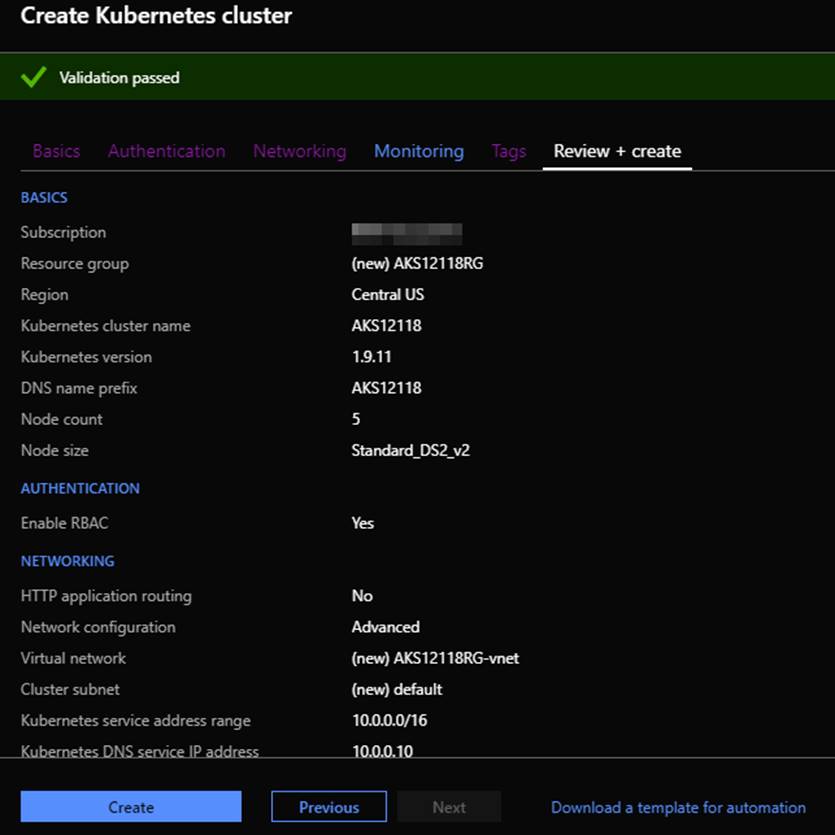
After all the sections are completed the new AKS will need to validate. After it is validated click on Create.
Exploring AKS
After the AKS cluster is created you will see it in Azure under Kubernetes services.

Also you may notice two new resource groups in your Azure subscription. The first resource group will be the one you created during the AKS creation. This is the resource group that will contain the Azure K8s cluster service. If you selected an advanced network configuration during deployment to create a new VNet you will see that as well.

You will also see a second resource group with a name format similar to MC_ResourceGroupNAME_AKSClusterNAME_REGION. As shown in the following screenshot I have a resource group named MC_AKS12118RG_AKS12118_centralus. This resource group contains the individual AKS cluster resources such as the nodes.
This resource group also contains supporting Azure services like DNS, public IP’s, storage, load balancers, network security groups and more. Note do not make changes to the resources in this resource group directly. You should only make changes through the AKS service and K8s itself. For example when you deploy a new load balancer service in K8s the corresponding Azure load balancer will automatically be created.

Access Kubernetes Dashboard
Next you can access the K8s cluster via a shell or access the dashboard. Before you can access the dashboard the service principle account that was created during the AKS deployment will need a ClusterRoleBinding that assigns the K8s role dashboard-admin it. Run the following syntax from the Azure cloud shell to do this:
kubectl create clusterrolebinding kubernetes-dashboard -n kube-system --clusterrole=cluster-admin --serviceaccount=kube-system:kubernetes-dashboardIf the service principle account does not have the K8s dashboard-admin role you will see the following error when accessing the dashboard:

After the service principle account is all set go ahead and run the following syntax from Azure cloud shell.
az aks browse --resource-group CLUSTERRESOURCEGROUPNAME --name NAMEOFTHEAKSCLUSTERRunning that syntax will output a URL similar to the one shown in the following screenshot. Click on this and it will open the K8s dashboard in a new browser tab.

The following 3 screenshots show some of the K8s dashboard.



That wraps up this blog post. I hope you were able to follow along and now have an AKS cluster up and running. In the next blog post I will go into deploying MySQL DB and WordPress Containers on AKS along with the services needed to access them. In that post we will spend time working with kubectl commands in the shell.


1 thought on “Getting Started with Azure Kubernetes Service (AKS)”