In this post I will explain the steps I had to take to allow DPM traffic in and out of my ISA firewall. (NOTE: This will also work with TMG 2010). This is required in order for a Secondary offsite DPM server to backup a Primary DPM server that is inside the local network and for client protection over the WAN. Both DPM offsite protection and offsite client protection are done via VPN. Configuring ISA / TMG for DPM traffic can seem somewhat complex and there is not any really good documentation on how to do this. My goal of this post is to simply this process as much as possible in clear easy to follow steps. I will assume that if you are reading this post that you are somewhat familiar with ISA 2006 / TMG 2010.
The steps needed to configure ISA 2006/TMG 2010 to allow DPM traffic in and out of the network are:
- Configure an access rule for DPM traffic.
- Define protocols in ISA/TMG for DPM traffic.
- Unrestrict RPC security.
1. Configure an access rule for DPM traffic.
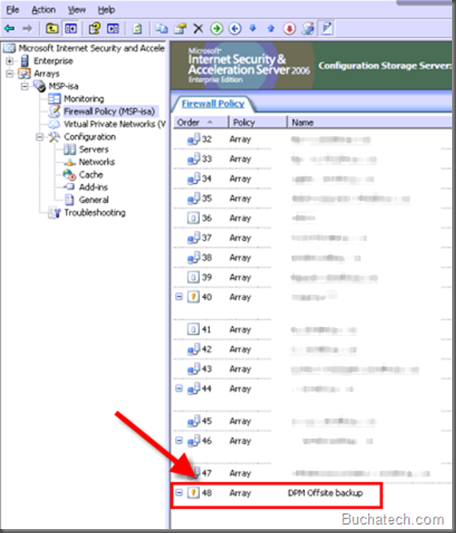
You first need to create an Access rule in ISA 2006 for DPM. I called mine DPM offsite.
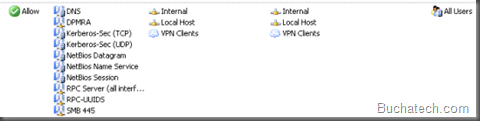
In the rule allow access to and from Internal, Local Host, and VPN Clients. We will add the protocols next.
2. Define protocols in ISA/TMG for DPM traffic.
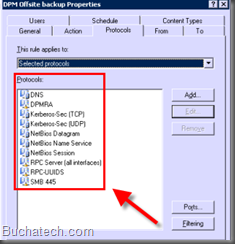
Now you need to add a bunch of protocols to your DPM access rule. Some of these protocols already exist and some of the protocols will be custom therefore you will need to create them. I will show you what needs to be created in the custom protocols.
Protocols that need to be added in your access rule for DPM in ISA 2006 / TMG 2010 are:
- DNS
- DPMRA (Custom protocol see the ports that need to be added for this below)
- Kerberos-Sec (TCP)
- Kerberos-Sec (UDP)
- NetBIOS Datagram
- NetBIOS Name Service
- NetBIOS Session
- RPC Server (all interfaces)(This is DCOM)
- RPC-UUIDS (This is a custom protocol that contains UUID’s for DPM)
- SMB 445 (Custom protocol for service message block)
Here are the ports that are used in the above protocols:
- DNS 53/UDP
- DPMRA 3148/TCP 3149/TCP 5718TCP 5719/TCP – 3148/UDP 3149/UDP 5718/UDP 5719/UDP
- Kerberos 88/UDP 88/TCP
- NetBIOS 137/UDP 138/UDP 139/TCP
- DCOM (RPC Server) 135/TCP Dynamic
- SMB 445/TCP
- RPC-UUIDS 135/TCP (This protocol also needs the UUID’s for DPM added to it.)
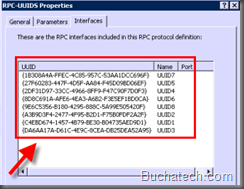
In the RPC-UUIDS custom protocol the following UUID’s need to be added:
MSDPM AC:
- {C4EBD674-1457-4B79-BE30-B04735AED9D1}
- {A3B9D3F4-2477-4F95-B2D1-F75B0FDF2A2F}
DPM RA:
- {DA6AA17A-D61C-4E9C-8CEA-DB25DEA52A95}
- {2DF31D97-33CC-4966-8FF9-F47C90F7D0F3}
MSDPM:
- {27F60283-447F-4D5F-AA84-F45D09BD06EF}
- {8D8C691A-AFE6-4EA3-A6B2-F3E5EF1BD0CA}
DPM LA:
- {1B308A4A-FFEC-4C85-957C-53AA1DCC696F}
- {9E6C5356-B180-4295-888C-5A99E505420F}
When you are done you should have a total of 8 UUID’s like in the following screen shot.
TechNet article on DPM and firewall ports: http://technet.microsoft.com/en-us/library/bb808766.aspx .
3. Unrestrict RPC security
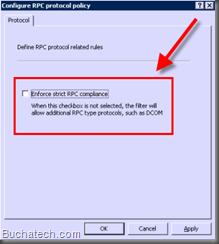
By default ISA / TMG enforces strict RPC security on all firewall rules and on the system policy. We need to unrestrict this security some in order for DPM traffic to flow between the DPM agents and the DPM server through the firewall. This needs to be done on the DPM access rule and your VPN access rule. Here are the steps:
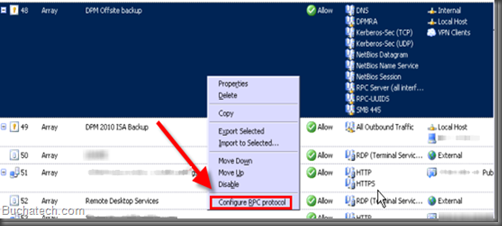
Locate your access rule in the firewall list and right click on it. Select Configure RPC filter.
A dialog window will pop up. Uncheck Enforce strict RPC compliance. Click OK.
In All Firewall Policy make sure that your access rule for DPM is at the top of the firewall rules. To do this right-click the access rule for DPM, and then click Move Up. Keep doing this until it is listed at the top of the list.
Make sure to apply your changes in ISA. Click Apply in the top pane of ISA/TMG to save your changes and update the configuration.You should now be able to communicate from DPM to clients or Secondary DPM servers offsite through VPN.
For more information Microsoft has created a video on this process: http://blogs.technet.com/b/dpm/archive/2010/12/06/new-video-tmg-setup-for-dpm-communication.aspx .


Here is a link to a post on how to change the default DCOM ports in case cannot or do not want to use the default DCOM ports.
http://www.scdpm.se/changing-dcom-ports/